|
|
| |
What is Information Security?
Information is an asset to all individuals and
businesses. Information Security refers to the
protection of these assets in order to achieve
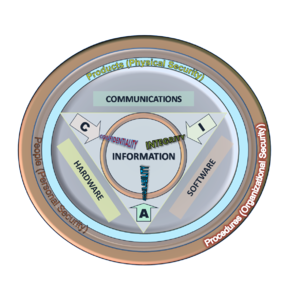
C - I - A as the following diagram:
|
Most
people, when they hear the term “information security”, usually focus on single
events like website hacking, procuring credit card details, email viruses or
the like. Most people immediately think
of some incident in which they themselves were the victim.
The fact
is that these are only the tips of the information security iceberg. To fully
appreciate the importance and scope of information security we need to widen
our view considerably. Information
security is more than just IT security. The focus of information security is
not on the security of an organisation’s IT operations per se, but on the
organisation’s ‘Information Assets’.
Information
assets’ can be a variety of items such as;
- business records
- client and contact databases
- personnel information
- financial records and
transactions
- information databases
- e-commerce transaction
details
Most
people underrate information security because they don’t see it from this wider
perspective. Information security covers
the whole of an organization's information.
How should I think of information security?
There are
three letters to remember when thinking of information security; they are C I
A. This has nothing to do with men in
black suits. CIA stands for Confidentiality,
Integrity and Availability, the three main checklist items when considering
information security. Try them now:
Confidentiality.
Can you guarantee that your confidential information will remain
confidential or is it open to compromise by unauthorized persons gaining access
to it? This access does not have to be
deliberate or malicious, it could occur accidentally because you have provided
insufficient control over its access.
Regardless of the intent, the impact can be just as devastating to a
business.
Integrity. Can you guarantee that all your
information will remain free from unauthorized change so that it can always be
relied upon for accuracy. Again, this
does not have to be deliberate. Without
adequate control, well-meaning but unauthorized staff can alter data without
malicious intent.
Availability. Can you guarantee that your
information (whether confidential or not) will always be available to those who
need it, when they need it. There are
few things more disruptive to business than for the staff being unable to
access the computer system for a period.
This last
point raises the unpopular twin spectra of Business Continuity and Disaster
Recovery. What if your entire premises are destroyed? What are the critical parts of your business
activities? How long would it take to reconstruct your entire IT infrastructure
on another site? What resources would
you need to do it? What critical systems
would you need first, what systems can wait?
You need a plan which enables your staff to quickly assess damage, and
institute a planned recovery process.
This process may go as far as the establishment of a mirror site where
critical IT resources are duplicated.
It is
common to view this scenario as an 'acceptable risk', that is, it can’t happen
to me. It will continue to be viewed as
an acceptable risk – that is, until it happens.
Then it is an unacceptable risk. But too late!
The CIA
principles should guide your thinking about information security. Remember that a security breach need not be a
malicious act; it could be as innocent and simple as a power outage or a
failure to set network access privileges correctly, or it could be the total
loss of all your facilities through a disastrous event, natural or unnatural.
What do I do about it?
The only defense you have against such events is to:
Deter.
Have in place the means to avoid or prevent the occurrence of
preventable information security breaches.
Protect.
Be in a position to safeguard
your information assets from security breaches.
Detect.
Equip yourself to rapidly detect the occurrence of security breaches.
Respond. Be ready to react to rapidly overcome the effects of security
breaches.
Recover. Be able to restore the integrity, availability and confidentiality
of information assets to their expected state.
Web applications are a major point of vulnerability in organizations today. Web app holes have resulted in the theft of millions of credit cards, major financial and reputation damage for hundreds of enterprises, and even the compromise of thousands of browsing machines that visited Web sites altered by attackers.
What do we understand by Information security and Ethical hacking?