Software developers looking to kickstart (or simply brag about) their security have a common trick up their sleeve: give away prizes
to successful crackers. Redact is trying just such a strategy with its
Secure Messenger app for iOS. It's offering £10,000 ($15,482) to anyone
who can visit London and successfully intercept an encrypted message
delivered through the company's peer-based, PIN-to-PIN communication
system. Entrants have until June 1st to prove that they're worthy of
making an attempt. Redact has more reason to hope we lose beyond its
pride and a big fat check, however -- it wants approval for handling the
UK government's secure data, and it wouldn't hurt to have proof that
the app design is airtight. If you're convinced that it's all just
bluster, you can challenge the company yourself at the source link.
Information Security, Ethical Hacking, website Security, Database Security, IT Audit and Compliance, Security news, Programming, Linux and Security.
Thursday 2 May 2013
Fake Microsoft Security Scam

The security firm reported detecting a number of scams targeting users with malware-laden messages masquerading as alerts from Microsoft in a blog post on Tuesday.
"Recently we have seen an increase in fake Microsoft scams, which function by tricking people into thinking that their PC is infected," wrote Webroot's Roy Tobin. He added that the cyber crooks use a variety of techniques to get the messages in front of their victims.
"There are a number of ways to figure out that this is a false alert. The first is that it's a website message and not a program; the second is that location of the website will be a random string of letters," he said.
"These websites will normally only stay active for 24-48 hours before they are pulled down. The websites' primary function is to get you to run a ‘removal tool' called ‘security cleaner'. This file is the infection and, if ran, will infect the PC and start displaying pop-ups."
The Webroot researcher said that the scams are not terribly advanced, and as long as users don't click on the malicious messages they will stay safe.
"At this stage [when the message appears], the PC is not infected so it's safe to close the browser and ignore any alerts from the website. Noting the website that displayed the message is good idea as you can notify the webmaster (if it's a legitimate website)," wrote Tobin.
Microsoft is one of many big brands used by cyber criminals to make the phishing messages look more legitimate. Last month, McAfee detected a cyber scam that used Facebook and LinkedIn to spread malware.
At the time of publishing, Microsoft had not responded to V3's request for comment on the influx of new scams using its name.
Analysis:
With these types of scams there are a number of things to remember.
1. Microsoft will never call you telling you that your PC is infected
2. Never allow strangers to connect to your PC
3. Do not give any credit card info to somebody claiming to be from Microsoft
4. If in doubt, shut down your PC and call Webroot
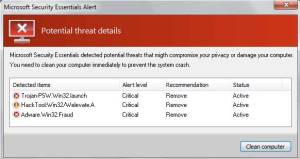
The current scam will display a webpage that is very similar to the one in Figure 1.
There are a number of ways to figure out that this is a false alert.
The first is that it’s a website message and not a program; the second
is that location of the web site will be a random string of letters.2. Never allow strangers to connect to your PC
3. Do not give any credit card info to somebody claiming to be from Microsoft
4. If in doubt, shut down your PC and call Webroot
More details:
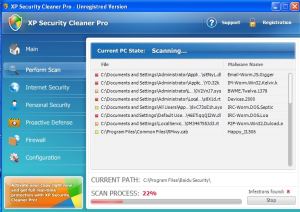
These websites will normally only stay active for 24-48hrs before they are pulled down. The websites’ primary function is to get you to run a “removal tool” called “security cleaner”. This file is the infection and, if ran, will infect the PC and start displaying pop-ups (like the one in Figure 2).
Figure 1: Fake Alert
At this stage, the PC is not infected so it’s safe to close the
browser and ignore any alerts from the website. Noting the website that
displayed the message is good idea as you can notify the webmaster (if
it’s a legitimate website).I have seen examples of this type of fake webpage being linked from advertising links. Using a browser that has a pop-up blocker will reduce the likelihood of encountering a bad advertising link. With scams like this, the most important way to stop getting infected is to be diligent when you’re online.
If a website asks you to run a file that you
haven’t asked for, be extremely cautious. The same goes for emails
(even from friends). Do not open executable files unless you are 100%
sure they are good.
Figure 2: Fake AV Pop-up
Behavior:
The info below is only a guideline as the payload can change.
However, it follows the same pattern of dropping a fake AV that stops
you from opening most programs.- Drops a randomly named file in the current users folder (Fake AV payload)
- Creates a service for the above file
- Disables Windows Firewall or modifies the settings to allow the file full access to the PC
- Creates a number of files in the windows recycler folder (usually Zero Access)
- Flags any opened program as an infection (by modifying the open shell reg key)
- Fake AV will then prompt the user to pay to remove the detected “infections”
Infection detected:
c:\users\owner\appdata\local\microsoft\windows\temporary internet files\content.ie5\wckxi56g\security_cleaner[1].exe
MD5: 68D9F9C6741CCF4ED9F77EE0275ACDA9
Detection rate of the file 28/46 Vendors on Virus Total.
Registry Changes:
Below is an example of some of the changes. The first shows how it modifies the open shell command so when you open any file it will run the Fake AV. The second shows the security center notifications that are disabled.
hkcr\w1\shell\open\command”C:\Users\User\AppData\Local\gpt.exe
hklm\software\clients\startmenuinternet\iexplore.exe\shell\open\command
HKLM\SOFTWARE\Microsoft\Security Center AntiVirusDisableNotify 00000001
HKLM\SOFTWARE\Microsoft\Security Center AntiVirusOverride 00000001
How to protect yourself from these scams:hklm\software\clients\startmenuinternet\iexplore.exe\shell\open\command
HKLM\SOFTWARE\Microsoft\Security Center AntiVirusDisableNotify 00000001
HKLM\SOFTWARE\Microsoft\Security Center AntiVirusOverride 00000001
There are a number of ways to ensure your PC is protected from these types of scams. The first step is simply being aware that these scams exist! Also, make sure to:
- Use Webroot Secure Anywhere
- Keep Windows updates turned on and set them to automatically update
- Use a modern secure browser like Firefox or Chrome
- Update any 3rd party plugins (Java/Adobe Reader/Flash player)
- Use an ad-blocker add-on in Firefox/Chrome
Removal:
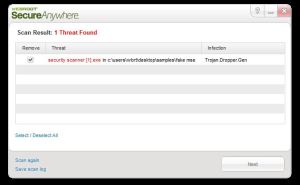
Webroot SecureAnywhere automatically blocks the installation of the infection so it won’t even run (Figure 3). If the PC has no AV software installed, booting into Safe Mode with networking and installing Webroot Secure Anywhere will remove the threat. Manually removing this threat is possible; however, there may be some system damage that will need to be repaired.
Webroot support is always available to help with removal and questions regarding this infection. Please visit the Webroot support web site for more detail at: http://www.webroot.com/support/.
Figure 3: SecureAnywhere Removal
Chinese hackers hijack US government website to spread malware

"During the last few hours we have identified that the US Department of Labor website has been hacked and it is serving malicious code," he said. Blasco said that the company is still in the process of investigating the attack, but that it is clearly designed for espionage.
"All we know is the following: the attackers gained access to the US Department of Labor website. They modified some files in the website so when a user visits the website some malicious code will be loaded from a malicious server. This malicious code collects information about the victim's system (Software installed, versions, etc)," Blasco told V3.
He said the firm has also detected a second function in the attack code, instructing it to target a patched vulnerability in Microsoft's Internet Explorer.
"If the vulnerability is exploited a backdoor is installed in the system. That backdoor communicates with a malicious server and the attackers can actually send orders to the system such as uploading and downloading files, executing commands, installing new malware," he explained.
The attack sends the hackers useful information like what security programmes the infected system has, what Java and Flash version is being used. The information could be used by the attackers to improve the effectiveness of future attacks on the infected machines system.
AlienVault reported tracking the attack to China, adding further fuel to the war of words going on between it and the US. The two countries have accused one another of mounting attacks on their networks for several years.
This reached new heights earlier this year when security firm Mandiant reported linking an advanced cyber campaign targeting the US government to a Chinese military unit.
More recently, Verizon claimed Chinese hackers are responsible for 96 percent of the world's active cyber espionage campaigns in its Data Breach Investigations Report 2013. China has consistently denied all allegations, saying cyber attacks are a problem that all governments face.
Phishing scam targets Apple ID users

Apple users are being
warned to stay vigilant following the discovery of a new series of
phishing attacks targeting the Apple ID network.
Researchers at Trend Micro have uncovered
a series of compromised sites that are being used to host fake login
pages. Designed to resemble the Apple ID login screen, the pages ask
users to enter both their usernames and passwords.
The compromised credentials are then believed to be harvested by the attackers for future use in account thefts.
Researchers noted that the phishing sites
have been connected to a spam campaign as well. Designed to resemble an
official Apple notification, the messages attempt to direct users to
the phishing sites by warning of an impending account removal.
"We’ve seen attacks targeting not only American users, but also British and French users," wrote Paul Pajares, Trend Micro's fraud analyst.
"Some versions of this attack ask not
only for the user's Apple ID login credentials, but also their billing
address and other personal and credit card information."
Though the pages themselves are designed
to closely resemble the Apple ID site, researchers note that the address
information itself can easily be spotted. Aside from not matching
Apple's own domains, the pages do not use the secure connection required
by Apple to log into its ID platform.
In addition to using best practices to
avoid spam sites, users can protect themselves from account theft by
activating Apple's new two-factor authentication platform.
Introduced by the company last month, the
security tool pairs an account with a user's mobile phone and asks for a
one-time use numerical code, which is sent via SMS. Such two-factor
controls have long been advocated by security experts for their ability
to prevent account loss even when a user's login credentials are stolen.
Former Obama CTO slams Twitter over lack of two-factor authentication

Harper Reed (pictured above), who managed the technology team overseeing the president's 2012 campaign, said they regularly contacted Twitter to ask for the capability, but were ignored, for reasons that remain unclear.
“I think it’s ridiculous. It was something we constantly called and complained about but apparently they didn’t want to,” he said at an event organised by the Direct Marketing Association.
“The only thing Twitter does is monitor verified accounts so we had that but two-factor authentication is one of the most important things for email and social.”
The comments come as the demand for two-factor authentication from Twitter grows in the wake of numerous high-profile hacks on account such as Burger King, Jeep and the Associated Press.
As such, Reed urged any firm using services that have two-factor authentication capabilities, such as webmail systems or Facebook to take advantage of the protection this offers.
“If you’re a brand on Facebook or using internal or external email systems that have two-factor authentication, please turn it on,” he added.
Reed also explained that the campaign team were deeply concerned by security issues during the re-election campaign, given the rise of hacking incidents and the methods of putting information online, used by groups such as Anonymous.
“We weren’t so worried about people stealing information but about information being leaked and the embarrassment that would cause to the Obama campaign,” he said.
Calls for Twitter to add two-factor authentication have been growing in recent weeks but so far the firm appears unmoved.
Researchers warn of shoddy security in surveillance cameras

Users and administrators
are being warned to update firmware for certain IP-enabled surveillance
cameras following the discovery of security flaws that could allow an
attacker to remotely spy on video streams.
Researchers from Core Security said they
have uncovered serious flaws in camera models from D-Link and Vivotek,
which included remote access to camera feeds and the ability to control
hardware.
According to Core Security, its
researchers have uncovered a number of flaws in both companies'
platforms, which could also be exploited to remotely install and execute
code on a targeted unit and harvest account credentials from a
compromised system, potentially opening the door for a much larger
attack.
Researchers also pointed out a number of
sloppy security practices in the firmware of the camera units, such as
hardwiring in set passwords and storing account credentials and access
keys unencrypted as clear text. Other flaws were found to yield user
credentials through memory dumps.
Core Security said that it has worked
with D-Link to deploy a patch for the affected models, though other
units could potentially by impacted by similar security issues. The
company did not receive any word back from Vivotek.
Security researchers have in the past
warned of security holes resulting from poorly secured appliances and
peripheral devices. IP-enabled appliances such as printers and scanners can be vulnerable to similar attacks that could allow an outside attacker to snoop on network activities and corporate data.
Paul Ducklin, head of technology in the
Asia Pacific region for Sophos, said that the fundamental nature of many
of the flaws was a particularly egregious offence on the part of the
vendors themselves. He advised administrators to keep peripheral devices
updated and to always be sure devices such as surveillance equipment
are as secure as other network components.
"Security patches for hardware devices like routers, printers and cameras are often overlooked," Ducklin wrote.
"Always-on devices like routers and
cameras are typically part of your security infrastructure, so a
compromise on one of them could facilitate the compromise of your whole
network."
Ramnit sleeping malware targets UK financial sector

"Trusteer's security team recently analysed a Ramnit variant that is targeting a UK bank with a clever one-time password (OTP) scam," said a Trusteer spokesman.
The malware reportedly avoids detection by going into an idle sleep mode until its intended victim logs into their online bank account, at which point it activates and presents them with a fraudulent phishing message.
"While the user is reading the message, Ramnit connects to its command and control server and obtains the details of a designated mule account," explained a Trusteer spokesman.
Once connected to the account the malware enters its final stage, presenting its victim with a second bogus message designed to dupe the user into entering a code that will let the malware bypass the system's final defence.
"This is followed by the initiation of a wire transfer to the money mule. But, there is still one more obstacle in the way of the malware – to complete the transaction a One Time Password (OTP) must be entered by the user. To overcome this requirement Ramnit displays [a second message]," said the spokesman.
"The temporary receiver number in the message is in fact the mule's account number. The user then receives the SMS and thinking that he must complete the "OTP service generation", enters their OTP. By entering the OTP, the user unknowingly enables the malware to complete the fraudulent transaction and finalise the payment to the mule account."
Trusteer said the malware's authors have moved to further hide the malware from its intended victims, by making it alter the bank's FAQ to make it seem as if the bogus messages are entirely legitimate.
"The new process Ramnit created may raise the suspicion of users who are accustomed to a specific workflow on their bank's website. Anticipating that some suspicious users may reference the bank's FAQ page, Ramnit authors took the extra step of altering the FAQ section to fit the new process," said the spokesman.
"By changing multiple entries in the FAQ section Ramnit demonstrates that its authors did not leave anything to chance – even if the victim decides to go the extra step, Ramnit is already there."
The Ramnit variant is one of many advanced attacks discovered this year. Prior to it Eset uncovered a malicious cyber campaign using a backdoor exploit in Apache web servers to herd web users to sites carrying Blackhole exploit packs.
Subscribe to:
Posts (Atom)