It is very easy to hack the Nasdaq according the
security expert Kolochenko that reported numerous vulnerabilities in
the official website of the exchange.
Just 10 minutes could be sufficient for an
attacker to hack the Nasdaq Stock Market, this is the alert provided
by Ilia Kolochenko, head of Swiss information security company High-Tech
Bridge. The security expert repeatedly warned Nasdaq.com on the risk
related to a cyber attack against one of most important stock exchanges.
The hackers could hit the financial world in various ways, targeting
clients and
trading platforms has revealed a few months ago by security firm Group-IB. That hackers could steal sensitive data for victims as
alerted Kolochenko, the expert highlighted that the Exchange has done nothing to preserve the security of its customers.
“A good hacker can get full
access to Nasdaq.com in a couple of days with the ability to do almost
whatever he wants, such as push an announcement that Facebook shares
have dropped 90%, [which] could cause havoc on the stock exchange.” “It
is quite frightening when you think about it. I discovered these
vulnerabilities in just 10 minutes with a Firefox browser without any
special tools or software.” “What is shocking is their attitude and
ignorance of notifications, especially taking into consideration their
recent technical failure,” said Kolochenko
The intruders could hack the Nasdaq website gaining its complete
control, once compromised cyber criminals could serve a malware,
steal user’s browser history and cookies and perform
phishing attacks. The warning arrived in concomitance with the Nasdaq’s trading stop caused, according official sources, by a
“technical glitch” that shut it down for three hours on 22th August.
According many computer experts the incident could hide a concerning
truth, it could be caused by a politically motivated cyber attack, it is
not a mystery that stock exchange is considered a
critical infrastructure and for this reason privileged targets of
state-sponsored attacks. At about the same time as the Nasdaq’s technical problem, the
Syrian Electronic Army hit The New York Times’ website.
The cyber security expert Kolochenko was able to inject some code into the website without being detected.
“This means anyone could inject arbitrary HTML code into Nasdaq.com to display a fake Web form demanding credit card numbers and other personal information or to inject malware to infect PC users. The only limit is the hacker’s imagination.”
Code injection is just a way to hack the
Nasdaq, Kolochenko found another vulnerability would allow hackers to
hijack a Nasdaq.com website visitors to malicious websites that serve
malware designed to steal sensitive information.
The menace is also for the same employees of the stock exchange that could be easy victims of a
spear phishing
attack, Kolochenko sustains that another possibility to hack the Nasdaq
is to send a unique link in a private message to Nasdaq technical
support or administrators waiting for its click to steal confidential
information from the victim’s browser.
The representatives of Stock Exchange refused the Kolochenko’s allegations for
leak of security to protect official website:
“We take all information security matters seriously.
We work with leading security vendors and have a trained and
professional team that evaluates all credible threats across our digital
assets,” said the Nasdaq spokesman.
Security of web services such as the stock exchanges must be approached with serious consideration
Despite it is not a mystery that with a
Cross-Site Scripting (XSS)
an attacker is able to inject malicious code in the page of a
vulnerable website the number of successful attacks still increase.
Vulnerable websites expose company owners and its clients to concrete
risks to be hacked …
the provocatory title I have chosen is “Give me 10 minutes to hack the Nasdaq” is far from fantasy!
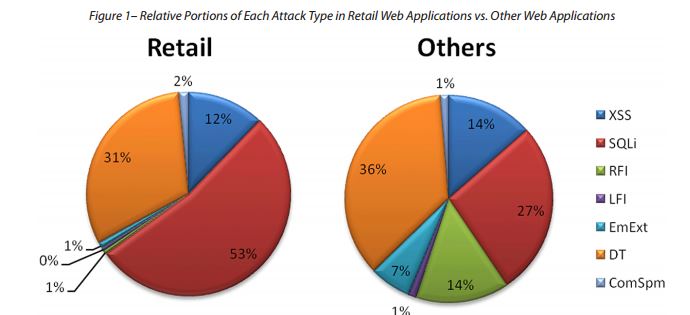
With an XSS attack the hackers can “phish” website visitors stealing their data, exploiting a
SQL injection flaw it is possible to access to the entire
database of a company with serious consequences.
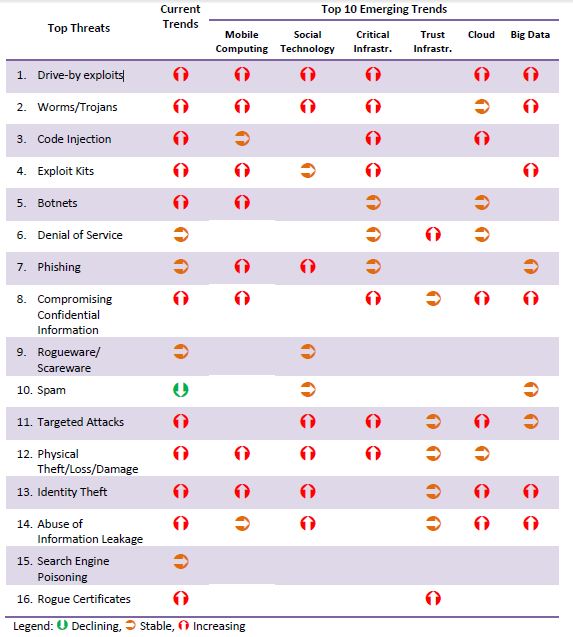
Last “ENISA Threat Landscape”
report issued early 2013 identified and listed the top threats and their trends, and concluded
that drive-by exploits have become the top web threat. Top 3 menaces according the ENISA report are:
To draw a picture of a current security landscape the document
contemplates data relates 120 recent reports, released from 2011 and
2012, from the security industry, CERTs, standardization bodies and
other independent parties.
Once again I decided to publish the conclusions the interesting Web Application Attack
report published by Imperva that provides an overview of the principal cyber security events occurred during the last 12 months.
The security of web application is an obligation, following a few recommendations for attack mitigation:
- Deploy security solutions that prevent automated attacks that are able to differentiate between automated bots and
human clients. Security procedures and solutions should be as automated
as possible to mitigate an attack volume that is too overwhelming for
humans to monitor.
- Share information and threat intelligence about cyber attacks.
- Detect and block attacks that target known vulnerabilities.
- Acquire intelligence on malicious sources to blacklist principal attack sources.
- Estimate countermeasures on the worst case scenario, not on the average case.