Today the official Vodafone Iceland was breached by group of hackers Maxn3y, left defaced and a heap of data leaked from its servers.
Vodafone Iceland was hacked by the group of hackers Maxn3y (@AgentCoOfficial) who in the past has stolen data from airports’ systems, electronic giants and fast food company.The hackers announced via Twitter to have successfully compromised Vodafone Iceland server and defaced the official website (vodafone.is) and various other sub domains including the company mobile site.
The hackers disclosed a compressed 61.7MB rar file which is locked with password TURKISH and that contains a collection of files including one titled users.sql that appears to contain the 77,000 user accounts. The file includes user names, social security numbers, encrypted passwords as many other encrypted information.
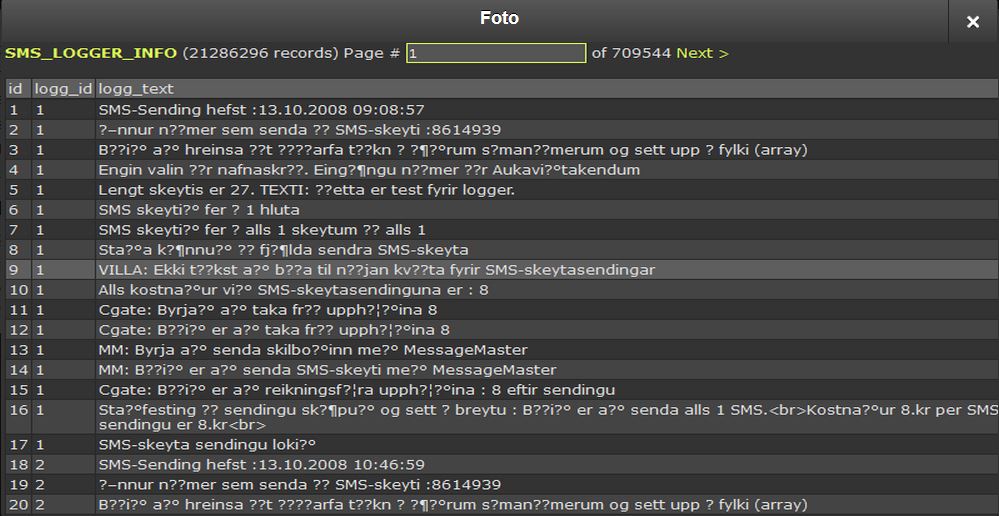
Another file, MySQL file greind.sql appears to contain a small log of sms history that is dated 2011 as well as a sms logger.
The portal CyberWarNews posted the list of files disclosed and provided information on their content.
Vodafone Iceland website was rapidly restored, but at time I’m writing it is not reachable.
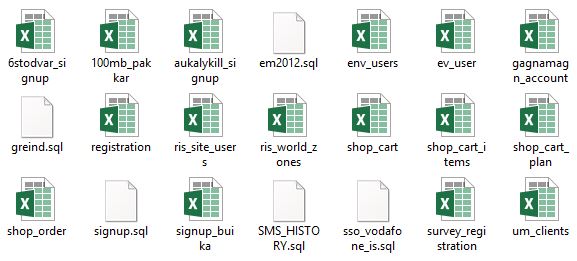
Following the complete list of files leaked.
v2.sql
Multi media database, nothing critical, 400K of user tracking and logging with user agents, refers etc.
greind.sql
sms history with what appears to be full text messages to a from numbers with timestamps, all dated 2011-08-19
SMS logger sender id, sms id, user ip, date.
900k rows of user contact details related to a SMS plan.
users.sql
user names, ids, encrypted passwords, email addresses, social security numbers, dates, bank details (alot is incomplete)
77,25
sso_vodafone.sql
account managers details
full names, phone numbers, email addresses.
sms_history.sql and signup.sql explained above.
XLS files
6stodvar_signup.xlskennitala (social security numbers), dates, ticket numbers, campaign ids(unknown campaign), email addresses
count: 23,494
100mb_pakkar,xls
id, code(unknown), msisdn, sms, timestamp(ts)
count: 1001
aukalykill_signup.xls
id, full name (nafn), kennitala(ssn), pnr, confirmed, date, ticket, email, senda, recivier.
count: 4305
env_users.xls
id, ipaddresses, user name, encrypted passwords, email addresses, first name, last name, phone, fax, reg date, last active, user level, notes
count: 334
ev_users.xls
id, school. login. clear text passwords, names, isadmin, active
count: 18
gagnamaga_account.xls
id, timestamp, ip, session id, social security numbers, email addresses
count: 1491
registeration.xls
id, phone, social security numbers, email addresses, tickets id, registration status, date, ip
count: 1247
ris_site_users.xls
user names, clear text passwords, names, email addresses and permissions
count: 12
shop_order.xls
cart_id, names, social security numbers, post codes, email addresses, credit card names, nulled credit card numbers and dates, sale amounts.
count: 3086
signup_buika.xls
real name, email addresses, company’s, chairman name.
count: 31
survey_registration.xls
id, content, date, email addresses
count: 1929
um_clients.xls
usernames,clear text passwords, active, company’s, full addresses, contact numbers, websites, nulled locations.
count: 767
vodafonecup2010
user names, 5x full names, phone numbers, social security numbers
count: 71
ris_world_zones.xls
names, partner countrys, to iceland (nothing important)
count: 10
shop_cart.xls
session id and details encrypted, (nothing important)
count: 49, 468
shop_cart_items.xls
file name says all, nothing of importance here.
shop_cart_plan
file name says all, nothing of importance here.