As Smucker’s referenced in its FAQ about the breach, the malware that hit this company’s site behaves much like a banking Trojan does on PCs, except it’s designed to steal data from Web server applications.
PC Trojans like ZeuS, for example, siphon information using two major techniques: snarfing passwords stored in the browser, and conducting “form grabbing” — capturing any data entered into a form field in the browser before it can be encrypted in the Web session and sent to whatever site the victim is visiting.
The malware that tore into the Smucker’s site behaved similarly, ripping out form data submitted by visitors — including names, addresses, phone numbers, credit card numbers and card verification code — as customers were submitting the data during the online checkout process.
What’s interesting about this attack is that it drives home one important point about malware’s role in subverting secure connections: Whether resident on a Web server or on an end-user computer, if either endpoint is compromised, it’s ‘game over’ for the security of that Web session. With Zeus, it’s all about surveillance on the client side pre-encryption, whereas what the bad guys are doing with these Web site attacks involves sucking down customer data post- or pre-encryption (depending on whether the data was incoming or outgoing).
IN GOOD COMPANY
When a reader first directed my attention to the Smucker’s breach notice, I immediately recalled seeing the company’s name among a list of targets picked last year by a criminal hacking group that plundered sites running outdated, vulnerable versions of ColdFusion, a Web application platform made by Adobe Systems Inc.
According to multiple sources with knowledge of the attackers and their infrastructure, this is the very same gang responsible for an impressive spree of high-profile break-ins last year, including:
-An intrusion at Adobe in which the attackers stole credit card data, tens of millions of customer records, and source code for most of Adobe’s top selling software (ColdFusion, Adobe Reader/Acrobat/Photoshop);
-A break-in targeting data brokers LexisNexis, Dun & Bradstreet, and Kroll.
-A hack against the National White Collar Crime Center, a congressionally-funded non-profit organization that provides training, investigative support and research to agencies and entities involved in the prevention, investigation and prosecution of cybercrime.
TOO MANY VICTIMS
Not all of the above-mentioned victims involved the exploitation of ColdFusion vulnerabilities, but Smucker’s was included in a list of compromised online stores that I regrettably lost track of toward the end of 2013, amid a series of investigations involving breaches at much bigger victims.
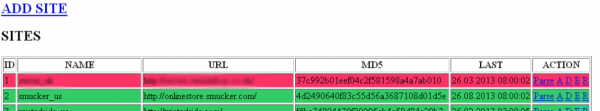
As I searched through my archive of various notes and the cached Web pages associated with these attackers, I located the Smucker’s reference near the top of a control panel for a ColdFusion botnet that the attackers had built and maintained throughout last year (and apparently into 2014, as Smucker’s said it only became aware of the breach in mid-February 2014).
The botnet control panel listed dozens of other e-commerce sites as actively infected. Incredibly, some of the shops that were listed as compromised in August 2013 are still apparently infected — as evidenced by the existence of publicly-accessible backdoors on the sites. KrebsOnSecurity notified the companies that own the Web sites listed in the botnet panel (snippets of which appear above and below, in red and green), but most of them have yet to respond.
Some of the victims here — such as onetime Australian online cash exchange technocash.com.au — are no longer in business. According to this botnet panel, Technocash was infected on or before Feb. 25, 2013 (the column second from the right indicates the date that the malware on the site was last updated).
It’s unclear whether the infection of Technocash’s secure portal (https://secure.technocash.com.au) contributed to its demise, but the company seems to have had trouble on multiple fronts. Technocash closed its doors in June 2013, after being named in successive U.S. Justice Department indictments targeting the online drug bazaar Silk Road and the now-defunct virtual currency Liberty Reserve.
SECUREPAY
One particularly interesting victim that was heavily represented in the botnet panel was SecurePay, a credit card processing company based in Alpharetta, Ga. Reached via phone, the company’s chief operating officer Tom Tesmer explained that his organization — Calpiancommerce.com — had in early 2013 acquired SecurePay’s assets from Pipeline Data, a now-defunct entity that had gone bankrupt.
At the time, the hardware and software that powered Pipeline’s business was running out of a data center in New York. Tesmer said that Pipeline’s servers had indeed been running an outdated version of ColdFusion, but that the company’s online operations had been completely rebuilt in CalpianCommerce’s Atlanta data center under the SecurePay banner as of October 2013.
Tesmer told me the company was unaware of any breach affecting SecurePay’s environment. “We’re not aware of compromised cards,” Tesmer said in an email. This struck me as odd, since the thieves had clearly marked much of the data they had stolen as “SecurePay” and listed the URL “https://www.securepay.com/” as the infected page.
Following our conversation, I sent Tesmer approximately 5,000 card transaction records that thieves had apparently stolen from SecurePay’s payment gateway and stashed on a server along with data from other victimized companies (data that was ultimately shared via third parties with the FBI last fall). The data on the attacker’s botnet panel indicated the thieves were still collecting card data from SecurePay’s gateway as late as Aug. 26, 2013.
Tesmer came back and confirmed that the card data was in fact stolen from customer transactions processed through its SecurePay payment gateway, and that SecurePay has now contacted its sponsoring bank about the incident. Further, Tesmer said the compromised transactions mapped back to a Web application firewall alert triggered last summer that the company forwarded to its data center — then located in New York.
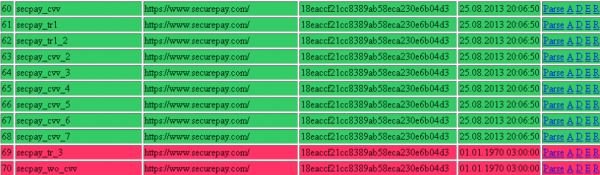
Several servers from credit card processing firm SecurePay were hacked by the ColdFusion botmasters.
Turns out, SecurePay also received a visit from the FBI in September, but alas that inquiry also apparently went nowhere.
“We did get a visit from the FBI last September, and they said they had found the name SecurePay on a list of sites that they were pursuing some big hacker team about,” Tesmer said. “I didn’t associate one with the other. We had the FBI come over and have a look at that database, and they suggested we make a version of our system and set that one aside for them and create a new system, which we did. They said they would get back in touch with us about their findings on the database. But we never heard from them again.”
Tomorrow, we’ll look at Part II of this story, which examines the impact that this botnet has had on several small businesses, as well as the important and costly lessons these companies learned from their intrusions.