Besides suspicion of unauthorised access to computer material, he was also arrested in connection with threats to kill and with swatting.
The South East Regional Organised Crime Unit (SEROCU) tweeted the arrest and gave a few more details in a release, saying that UK law enforcement worked closely with the FBI in the ongoing investigation.

Our Cyber Crime Unit has arrested an 18-year-old in connection with the #DDOS attach [sic] on #Xbox & #Playstation this morning working with @FBIIn further tweets, SEROCU said that the suspect was arrested under the Computer Misuse Act 1990 in an operation that focused not just on the gaming DDoS, but also on swatting: the practice of making bogus emergency calls, as pranks or acts of revenge against someone, that result in the dispatch of emergency services that can wind up with law enforcement surrounding innocent people's homes with guns drawn.
 Craig
Jones, Head of the Cyber Crime Unit at SEROCU, said that the swatting
took place in the US, with hoax emergency calls coming in via Skype and
resulting in a "major incident" in which SWAT (Special Weapons and
Tactics) teams were dispatched.
Craig
Jones, Head of the Cyber Crime Unit at SEROCU, said that the swatting
took place in the US, with hoax emergency calls coming in via Skype and
resulting in a "major incident" in which SWAT (Special Weapons and
Tactics) teams were dispatched.We don't yet know whether in fact this teenager was associated with Lizard Squad - just that police are investigating his involvement with the gaming attack.
What is Lizard Squad? It's often referred to as a 'hacking group', though as Naked Security's Mark Stockley has pointed out, the attack on millions of adults' and children's Christmas-day gaming fun doesn't qualify as a "hack" in the sense that it required no skills at penetrating Microsoft's or Sony's networks whatsoever.
In the final Chet Chat podcast of 2014, Mark explains [10'00"] that all the cyber vandals did was to cyberishly squat in front of the games so that few could get in to play:
This isn't a hack in the sense that we normally use the word hack to refer to some sort of breach or unauthorised entry. Lizard Squad didn't gain entry to any Microsoft data or Sony data. They didn't breach any Microsoft systems or Sony systems. They weren't picking the lock; they were barricading the door from the outside.This is the second arrest connected with the attack, following which the Lizard Squad has been blowing raspberries at authorities and shilling its takedown-for-hire DDoS service.
The first arrest was of Vinnie Omari, a 22-year-old who was bailed out on 30 December.
Two arrests? Pah. We haven't seen anything yet, Jones assures us:
We are still at the early stages of the investigation and there is still much work to be done. We will continue to work closely with the FBI to identify those to who commit offences and hold them to account.SEROCU, supported by the National Cyber Crime Unit (NCCU) and working closely with the FBI, arrested the teenager this morning in Southport.
Agents also seized a number of electronic and digital devices.

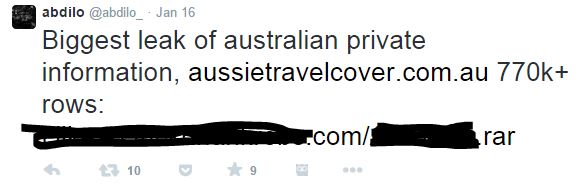
 Nearly 900,000 client records including names,
addresses, and phone numbers have been stolen from travel insurer Aussie
Travel Cover by a suspected member of the Lizard Squad hacking crew.
Nearly 900,000 client records including names,
addresses, and phone numbers have been stolen from travel insurer Aussie
Travel Cover by a suspected member of the Lizard Squad hacking crew.